In recent years, the widespread adoption of remote work has brought about many cybersecurity challenges for organizations worldwide, including the increased vulnerability of remote workers’ devices and networks to cyber threats. Unlike traditional corporate environments with enterprise-grade security measures, remote work setups often lack the same level of protection, leaving endpoints exposed to malware, phishing attacks, and other malicious activities. In many cases, employees use personal devices or unsecured networks in public venues to access corporate resources, expanding the attack surface further and increasing the risk of breach. Monitoring and controlling network traffic while also defending against data breaches has become increasingly complex for security teams.
The increase of hybrid and remote work, combined with the proliferation of cloud-based collaboration tools and applications, has dramatically increased potential vulnerabilities and opportunities for hackers. The numbers continue to grow:
- According to Gartner, by 2027, 75% of employees will acquire, modify, or create technology outside IT’s visibility — up from 41% in 2022.
- According to Sophos, “The State of Ransomware in 2023” report, ransomware affected 66% of organizations in 2023.
- Gartner reports that over 70% of companies surveyed have reported at least one cloud breach since 2022.
With increased risk, organizations have increased their spending in security for the home office. But even as organizations increase their resources, existing solutions are not always effective.
VPN Data Breach Vulnerabilities | Cybertronics Quantum-Resistant Cryptosystem
During and after the pandemic, VPNs became the de facto security solution for thousands of employees forced to work from home. Unfortunately, there are many problems with today’s VPNs.
Work from Home
Without CyberProtonics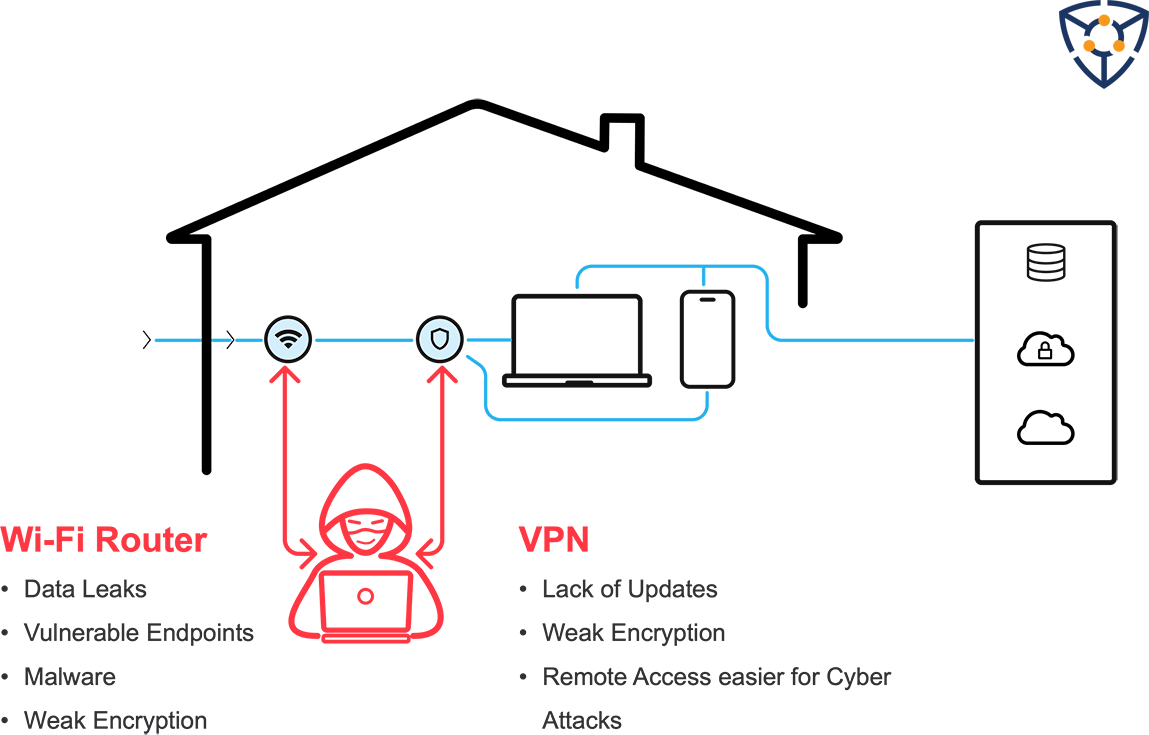
The first issue is the nature of the standard VPN setup. VPN clients are installed on employee laptops, establishing an encrypted network tunnel to protect sensitive network traffic between their devices, company networks, and the cloud. However, today’s encryption standards utilized by VPN providers often can create latency issues that interfere with employees’ ability to complete their daily tasks. Whenever an employee runs into an issue with the VPN, they can quickly turn it off. In addition, while using a VPN can protect data in transfer, it does nothing to protect data at rest once assets are parked on devices within the workers’ home networks.
Another vulnerability that exists is the lack of solid security on Wi-Fi routers. According to CyberArk’s remote work study, 77% of remote employees use unsecured Wi-Fi routers at home or in a public venue. These are a top target for hackers looking to intercept data traffic, perform man-in-the-middle attacks, or gain access to the devices connected to the enterprise network.
Quantum Computing Risks – CyberProtonics, The Cybersecurity Future
Cybersecurity experts believe that by 2025, quantum computing, which can break existing VPN encryption standards like ChaCha20-128, will arrive and that existing encryption will crumble within a few hours of a quantum attack. While it’s possible to increase the strength of the encryption to 256 bits to adapt for quantum, this immediately creates the problem of mass latency that would make it untenable for work-from-home environments.
Traditional home office cybersecurity solutions are playing a role in protecting from some data breaches, but what can be done to protect against the vulnerabilities in existing solutions and to prepare for the advent of quantum computing?
Data Breach Protection for The Home Office | CyberProtonics Partners with Simplifi
CyberProtonics has partnered with Simplifi to create a product that addresses today’s home office security vulnerabilities. It combines Simplifi’s “work from home” router with CyberProtonics’ quantum-resistant cryptosystem to create a “quantum tunnel” for all traffic— while working within the home office or in transit as it leaves the home network.
Work from Home
With CyberProtonics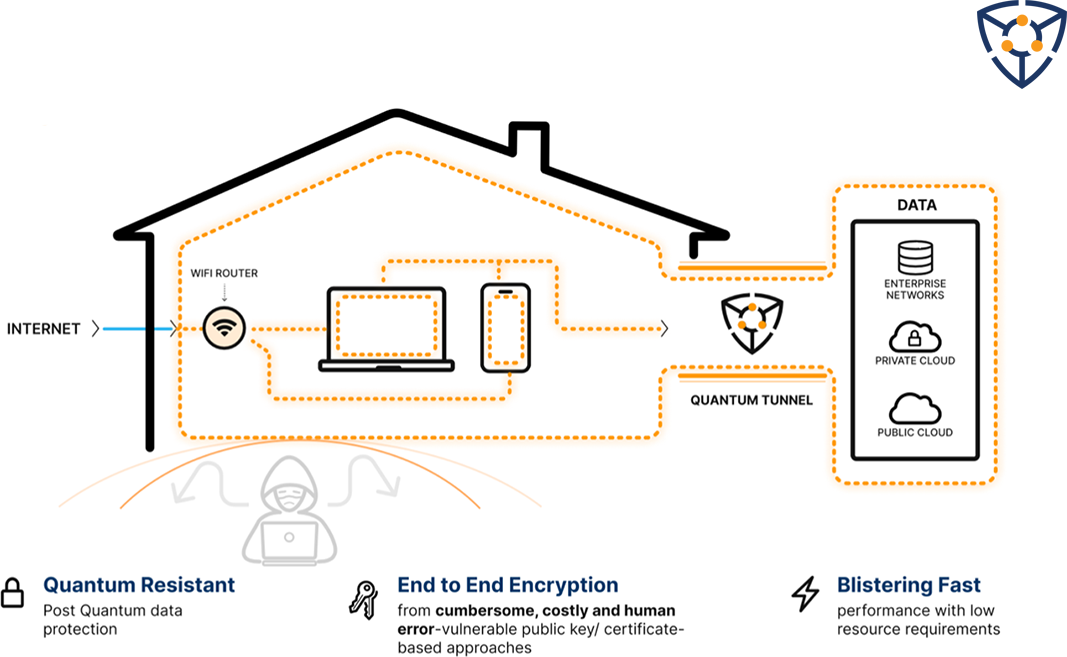
By utilizing CyberProtonics’ lightweight post-quantum encryption embedded within the router, employees can secure their work without any discernable latency and can’t toggle off the network tunnel. CyberProtonics’ quantum-resistant cryptosystem can be easily integrated with existing security solutions to fill current gaps, and includes key features to secure the home office against data breaches:
- lightweight enough for any device or location,
- utilizes key sizes that are smaller than 100 bytes
- sub-4 millisecond encryption speed
- encryption strength is stronger than existing encryption standards, including AES, RSA, and ChaCha20.
Zero Trust Security: The CyberSecurity Future
The future of quantum cybersecurity is expanding with quantum-resistant cryptosystems going beyond network traffic and addressing data at rest and zero trust.By integrating with zero trust security strategies—including identity management, threat intelligence capabilities, contextual behavior analysis, and least privileged access—CyberProtonics’ cryptosystem forms an impenetrable barrier around the most sensitive data, no matter where it lives.
How CyberProtonics Tackles
Working From Home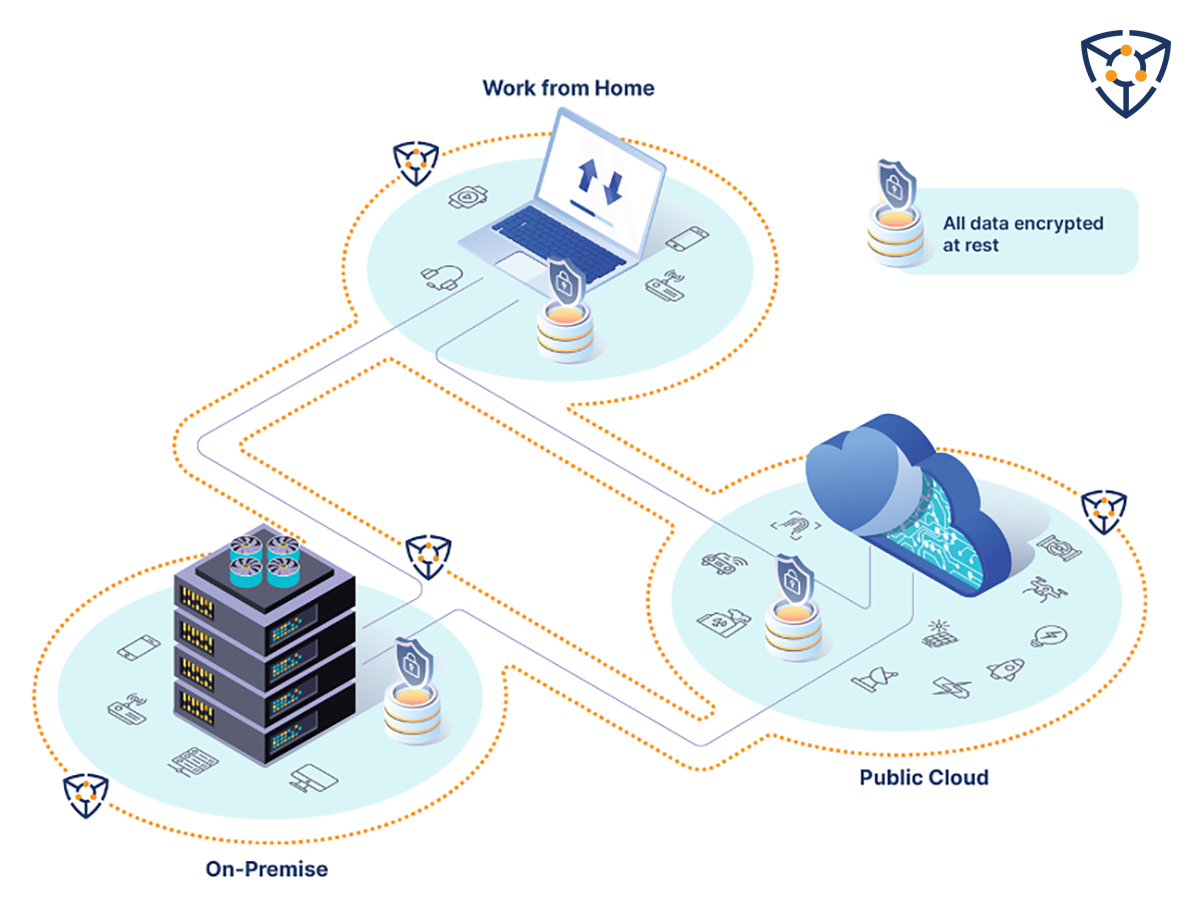
Even if all preventative measures (such as NDR, EDR, and passwords) fail, your data is always protected through contextual analysis and continuous verification of identity provided by a zero-trust ecosystem that won’t grant access to encrypted data—whether on a device, on-premises, at home, or in the cloud.
CyberProtonics’ cryptosystem provides an indispensable additional layer of security around your data. We are the invaluable measure that turns your precious data from a valuable ‘diamond’ into an unusable ‘bag of coal’ for those not authorized to view it.

Nick Morpus
Analytical Cyber Security Specialist and PMM. Nick is well-versed in SASE architecture, zero trust, post quantum cryptography, and general network security practices/experience.
Read more like this
-
SATCOM Security: Quantum Threats vs. Post-Quantum Cryptography
Imagine a future not too far off from our own. Envision a landscape where complex problems are effortlessly unraveled, and […]
-

What Telecom Companies Need to Know About the New FCC Breach Reporting Rule Changes
In a digital age where data security is paramount, regulatory bodies continually evolve requirements to keep pace with emerging threats. […]
-

A Quantum Future: A Crash Course on the Q-Day Around the Corner
Our modern forms of computing, also known as classical computing, have driven our societies to new heights by unlocking new […]
