Our modern forms of computing, also known as classical computing, have driven our societies to new heights by unlocking new levels of productivity never dreamed of in years past. While the results and benefits of classical computing are irrefutable, we are simultaneously understanding and reaching the limitations of this technology. In taking the next step, the need for more powerful and efficient computing is necessary to solve the ever more complex problems of today.
Ever since mathematician, Peter Shor, developed a quantum algorithm in 1994 ceremoniously named “Shor’s Algorithm,” interest in quantum computing spiked. Shor’s Algorithm demonstrated the capability to find the prime factors of seemingly enormous numbers far more efficiently than any current classical algorithm. Since then, untold amounts of money have poured into the development of a quantum computer capable of unimaginably complex computations. These investments are producing results, and it looks as though quantum computing is a real possibility in the very near future.
Without getting too into the weeds on superpositions, entanglement, and probabilities, quantum computing would far outpace the computational speed and power of even the most sophisticated classical supercomputers. Imagine a future where complex medical problems, defense strategies, and economic patterns are analyzed and extrapolated out to find solutions to issues that have baffled us for decades. That is the potential promise of quantum computing.
What is Q-Day?
Every technological development has its benefits and drawbacks, and quantum computing is no exception. Q-Day refers to the day when quantum computing reaches the compute power to unravel most of the cybersecurity protections and encryption standards that protect all of our major industries, infrastructures, defense apparatuses, and economic systems. The computational power of quantum and Shor’s Algorithm would effectively tear through popular encryptions that would’ve taken hundreds, thousands, or millions of years for classical computers to break, including:
- RSA
- ChaCha20-128
- AES-128
- And many more
Other encryptions theoretically can stand up to the large-scale factoring capabilities of quantum, such as AES-256 or higher, due to their larger bit strength and varying key lengths. More on that later though.
This isn’t a movie; this is a very likely possibility in the near future.
There are some experts that predict Q-Day as early as 2025. Whether or not that is true is irrelevant, because it is only a matter of time before we reach this milestone. The data guarded by existing encryptions are secure-ish for now, but once Q-Day comes, will that stolen or exposed data hold up against the power of quantum computing? Threat actors are counting on your old standards falling short.
What can be done to prepare for Q-Day?
By now it’s obvious that many of our existing encryption standards aren’t enough to protect against future threats, particularly quantum based. Even standards that are theoretically quantum-resistant also have their drawbacks that make their implementation unfeasible in today’s fast-moving business environment.
Take AES-256 as mentioned before. AES-256 is considered a quantum-resistant encryption standard due to the nature of its variably expanding key sizes. However, the impracticality of a wide implementation becomes apparent when considering the heavy computational demands this encryption requires. Productivity would grind to a screeching halt. This is precisely why AES-256 is not already implemented in every SQL database on the planet, let alone implemented to protect data-in-transit over networks.
Many other encryption standards are simply not up to the task of handing a future of quantum computing, with many failing in hours instead of years. If AES is not right for every situation and other encryption standards aren’t strong enough to fend off quantum powered brute force attack, what is the solution?
Introducing CyberProtonics Quantum-Resistant Cryptography
The CyberProtonics quantum-resistant cryptosystem on the other hand utilizes key sizes smaller than 100 bytes with a sub-4 millisecond encryption speed while maintaining an encryption strength stronger than that of the most popular encryption standards, including AES, RSA, and ChaCha20.
This means that CyberProtonics is stronger, lighter, and faster than any other option, quantum-resistant or not. The point is, there is no tradeoff with CyberProtonics. You get quantum-resistant encryption without any impact on performance now and when Q-Day inevitably comes.
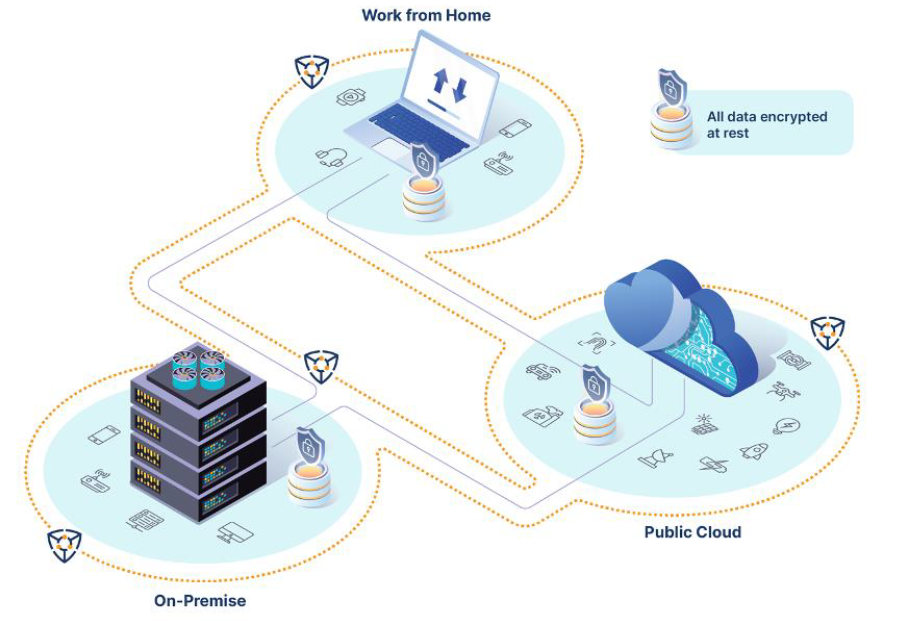
Let’s be honest, cyber breaches are occurring with or without quantum computing.
The traditional network perimeter is obliterated, work is conducted from everywhere, data moves all over the world to offices, to the cloud, to the phones in your pockets. The perimeter has evolved into what we know as the “edge,” where the security strategy has expanded outwards to protect data living on or accessed by endpoint devices, no matter where they are. Organizations are looking to protect their data whether it lives within the on-premises network or accessed by employee devices on the go.
CyberProtonics strengthens that edge by creating the true last line of defense if or when your other security measures fail by rendering breached and stolen data useless by attackers. Even now, hackers are breaking in and stealing data in the hopes of decrypting it later should they get their hands on tomorrow’s quantum capabilities.
We pour cold water on these hopes of “Steal now, decrypt later” by integrating with existing security strategies of least privileged and contextual-based access controls. Simply put, if you aren’t who you say you are, accessing this information on a device trusted and routinely verified, you will not decrypt this information.
We get to tell attackers “Take what you want, the data is useless to you,” and that’s a good feeling.
Where does CyberProtonics live?
CyberProtonics is not here to replace your existing security infrastructure. It’s important that you maintain your security controls and remediation policies. We are here to help you reinforce your existing infrastructure that acts as the last line of defense between attackers and your data. The best part of it is, we are also the strongest line of defense.
CyberProtonics Quantum-Resistant Cryptosystem slots in as the encryption barrier around your data in transit and at rest at the office, in the cloud, or at home.
Even better, our cryptosystem is so lightweight that it can operate on the smallest of IoT devices and legacy infrastructure, further securing the ever-expanding attack surface. This means our encryption not only useful in the office and in the cloud, but also at home, embedded in our valuable infrastructure, and hard at work protecting the devices that power our national defense.

Nick Morpus
Analytical Cyber Security Specialist and PMM. Nick is well-versed in SASE architecture, zero trust, post quantum cryptography, and general network security practices/experience.
Read more like this
-
SATCOM Security: Quantum Threats vs. Post-Quantum Cryptography
Imagine a future not too far off from our own. Envision a landscape where complex problems are effortlessly unraveled, and […]
-

What Telecom Companies Need to Know About the New FCC Breach Reporting Rule Changes
In a digital age where data security is paramount, regulatory bodies continually evolve requirements to keep pace with emerging threats. […]
-

Change Healthcare Breach: The Devastating Reminder of Healthcare Cybersecurity Shortcomings
In February 2024, Change Healthcare, one of the largest healthcare IT companies in the United States, fell victim to a […]
